ABSTRACT:
The most predominant computer authentication method is to use alphanumerical usernames and passwords whereas this method has been shown many major disadvantages. This is due to the problem that, users tend to choose passwords that can be easily guessed and hacked by the hackers. On the other hand, Considering the user have got a password which is difficult to guess, then it is difficult to remember. To overcome this kind of problem of low security, High end Authentication methods are developed by researchers that use images as crystal clear password. In our research, we conduct a comprehensive study on the existing graphical password techniques and provide a possible solution using Graphical password schemes which have been proposed as a possible alternative to text-based schemes. This is based on the human intelligence analysis such as, humans can remember pictures better than text; Pictures are generally very easy to be remembered or recognized than text. The high level concept is, user are permitted to click the portion of an image, each click results in showing a next-image, in effect leading users down a “path” based on the type and portion of click on their sequence of points. A wrong click by the fake user leads down in an incorrect path, with an explicit indication of authentication failure only after the final click. Fake users more than 2 attempts will be blocked from future access.
EXISTING SYSTEM:
• Security plays a major role in the authentication process in high severity applications. Passwords are the type of secret code used in the process of authentication.
• In the existing system, a captcha and picture based authentication is designed to authenticate into the system.
• The concept of visual cryptography has been integrated with the captcha for individual user and got splitted equally in order to store in the server.
• The Server provide authentication to the requestor thereby verifying the captcha by merging the splitted shares to ensures the authorized human interpretations.
• The authentication by means of picture also been the part of the existing methodology that has a feature of picture spot clicking password.
DISADVANTAGE:
PROPOSED SYSTEM:
• The projected system encompasses severe security outlook to design a secure authentication system.
• The concept of captcha to interpret the authorized human is incorporated that prevail the human inference with the server by cryptographic concepts.
• Image hotspot technique accompanying with the notion of captcha designs the system in enhanced way with security measure.
• Successive image hotspots have been designed by means of graphical representation or clued points on the image taken.
• On the thriving traversal of the 5 successive hotspot images, the user gets authenticated to the server.
• The successive traversal of hotspot image can been identified by pattern matching scenario in order to correlate the authorized user’s click points in the hotspot.
ADVANTAGE:
- The Advantages of the proposed system is to increase the multiple number of hotspot level to avoid the vulnerability of the system.
- Also the pattern matching technique used to identifying the authorized users based on our entered hotspot level.
ARCHITECTURE:
SCREENSHOT:


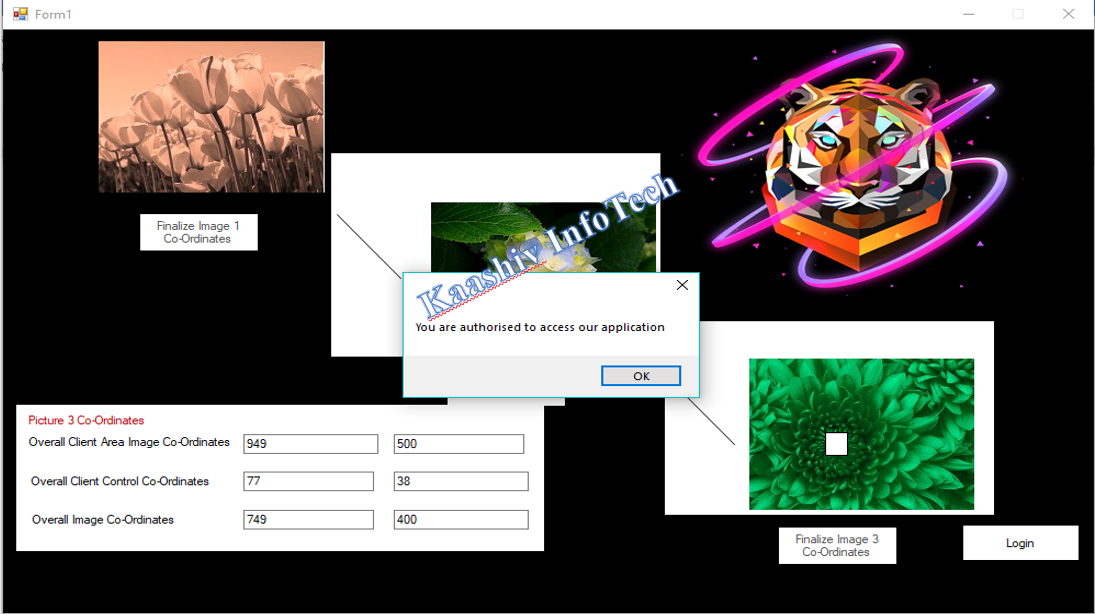
SAMPLE CODE:
using System;
using System.Collections.Generic;
using System.Linq;
using System.Security.Cryptography;
using System.Text;
using System.Data;
using System.Data.SqlClient;
namespace ObjectAccess
{
public class ConnectDB
{
SqlConnection conn;
private string sqlpri;
public string sql
{
get
{
return sqlpri;
}
set
{
sqlpri = value;
}
}
public void OpenDB()
{
conn = new SqlConnection(@"Data Source=KAASHIV-PC\KINFOTECH;Integrated Security=true;Initial Catalog=OntheUser");
//(ConfigurationManager.AppSettings["DBConnection"].ToString());
conn.Open();
}
public int VerifyAdminCredentials(string usrName, string pwde)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("sp_VerifyAdminCredentials", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@UserName", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@Password", SqlDbType.VarChar));
cmd.Parameters[0].Value = usrName;
cmd.Parameters[1].Value = pwde;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ((int)ds.Tables[0].Rows[0][0]);
}
public int VerifyDBACredentials(string usrName, string pwde,string dbaref)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("sp_VerifyDBACredentials", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@UserName", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@Password", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@DBAReferenceNumber", SqlDbType.VarChar));
cmd.Parameters[0].Value = usrName;
cmd.Parameters[1].Value = pwde;
cmd.Parameters[2].Value = dbaref;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ((int)ds.Tables[0].Rows[0][0]);
}
public int VerifyCredentials(string usrName, string pwd,string UserProfile)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("sp_VerifyCredentials", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@UserName", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@Password", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@UserProfile", SqlDbType.VarChar));
cmd.Parameters[0].Value = usrName;
cmd.Parameters[1].Value = pwd;
cmd.Parameters[2].Value = UserProfile;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ((int)ds.Tables[0].Rows[0][0]);
}
public int VerifyHighProfile(string passport, Guid RefNum)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("sp_VerifyHighProfile", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@PassportNum", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@RefNum", SqlDbType.UniqueIdentifier));
cmd.Parameters[0].Value = passport;
cmd.Parameters[1].Value = RefNum;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ((int)ds.Tables[0].Rows[0][0]);
}
public DataTable AddNewUser(string strFName, string strLName,
string UName, string Pwd, string DOB,
string Mobile, string SecurityQue, string SecurityAns,
string NativePlace,string PassportNumber,string MotherName,string BloodGroup,
string UserProfile)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("[sp_AddNewUser]", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@FirstName", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@LastName", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@UserName", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@Password", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@Mobile", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@DOB", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@PassportNumber", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@MotherName", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@BloodGroup", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@NativePlace", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@SecurityQuestion", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@SecurityAnswer", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@UserProfile", SqlDbType.VarChar));
cmd.Parameters[0].Value = strFName;
cmd.Parameters[1].Value = strLName;
cmd.Parameters[2].Value = UName;
cmd.Parameters[3].Value = Pwd;
cmd.Parameters[4].Value = Mobile;
cmd.Parameters[5].Value = DOB;
cmd.Parameters[5].Value = DOB;
cmd.Parameters[6].Value = PassportNumber;
cmd.Parameters[7].Value = MotherName;
cmd.Parameters[8].Value = BloodGroup;
cmd.Parameters[9].Value = NativePlace;
cmd.Parameters[10].Value = SecurityQue;
cmd.Parameters[11].Value = SecurityAns;
cmd.Parameters[12].Value = UserProfile;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ds.Tables[0];
}
public bool DoesUserExist(string username, string password)
{
OpenDB();
sql = "SELECT * FROM tblUserDetails WHERE UserName = '" + username +
"' AND Password = '" + password + "'";
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet dsResult = new DataSet();
string userExists = (cmd.ExecuteScalar() ?? "0").ToString();
return userExists != "0";
}
public string GetPublicKey(string Query)
{
OpenDB();
sql = "SELECT KeyGenerated FROM objectChangeScript where script = '" + Query+"'";
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0].Rows[0][0].ToString();
}
public DataTable GetTblCol(string tbl)
{
OpenDB();
sql = "select COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME = '" + tbl + "'";
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public DataTable GetPolicyTable()
{
OpenDB();
sql = "SELECT * FROM dbo.Table_Profile ";
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public DataTable JTAMGetPolicyTable()
{
OpenDB();
sql = "SELECT * FROM dbo.tbl_AccessPolicy";
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public DataTable JTAMGetPolicyTableYes()
{
OpenDB();
sql = "SELECT * FROM dbo.tbl_AccessPolicy where Access='Yes'";
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public int DBAInsert(string Uname, string PWD, string DBARefer, string GmailUser,string contactNumber)
{
OpenDB();
byte[] inputArray = UTF8Encoding.UTF8.GetBytes(DBARefer);
TripleDESCryptoServiceProvider tripleDES = new TripleDESCryptoServiceProvider();
string modified = Uname;
for (int val = Uname.Length; val <= 15; val++)
{
modified += " ";
}
tripleDES.Key = UTF8Encoding.UTF8.GetBytes(modified);
tripleDES.Mode = CipherMode.ECB;
tripleDES.Padding = PaddingMode.PKCS7;
ICryptoTransform cTransform = tripleDES.CreateEncryptor();
byte[] resultArray = cTransform.TransformFinalBlock(inputArray, 0, inputArray.Length);
tripleDES.Clear();
string myEncrptedText = Convert.ToBase64String(resultArray, 0, resultArray.Length);
StringBuilder randomText = new StringBuilder();
// string code;
string code;
Random r = new Random();
for (int j = 0; j <= 5; j++)
{
randomText.Append(myEncrptedText[r.Next(myEncrptedText.Length)]);
}
code = randomText.ToString();
string strCmd = "insert into DBALogin(UserName,Password,DBAReferenceNumber,GmailUserName,PrivateKey,ContactNumber ) values ('" + Uname + "','" + PWD + "','" + DBARefer + "','" + GmailUser + "','" + code + "','"+contactNumber+"')";
SqlCommand cmd = new SqlCommand(strCmd, conn);
int i = cmd.ExecuteNonQuery();
conn.Close();
return i;
}
public DataTable JTAMGetPolicyColumnYes(string tblName)
{
OpenDB();
sql = "SELECT * FROM dbo.JTAMSelectedColumn where tbl='"+ tblName + "'";
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public int UpdateTblAccessPolicy(string tbl_Name,string Policy_access)
{
OpenDB();
string strCmd = "update Table_Profile set [profile_access] ='" + Policy_access + "' where [table_name] = '" + tbl_Name +"'";
SqlCommand cmd = new SqlCommand(strCmd, conn);
int i = cmd.ExecuteNonQuery();
conn.Close();
return i;
}
public int JTAMUpdateTblAccessPolicy(string tbl_Name, string Policy_access)
{
OpenDB();
string strCmd = "update tbl_AccessPolicy set [Access] ='" + Policy_access + "' where [Name] = '" + tbl_Name + "'";
SqlCommand cmd = new SqlCommand(strCmd, conn);
int i = cmd.ExecuteNonQuery();
conn.Close();
return i;
}
public DataTable GetpgPolicies()
{
OpenDB();
sql = "SELECT * FROM dbo.SYS_POLICYTABLE where policy_name like '%pg_%'";
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public DataTable GetPolicies()
{
OpenDB();
sql = "SELECT * FROM dbo.SYS_POLICYTABLE where policy_name like '%sp_%'";
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public DataTable GetMemberPolicies()
{
OpenDB();
sql = "SELECT * FROM dbo.Member_ProfileDecide";
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public DataTable JTAMSelCol()
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("JTAMSelCol", conn);
cmd.CommandType = CommandType.StoredProcedure;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ds.Tables[0];
}
public void Flush()
{
OpenDB();
string strCmd = "delete from JTAMSelectedColumn ";
SqlCommand cmd = new SqlCommand(strCmd, conn);
int i = cmd.ExecuteNonQuery();
conn.Close();
}
//public void InsertObject()
//{
// OpenDB();
// string strCmd = "insert into tbl_CoOrdinates values ('" + tblname + "' ,'" + colname + "','" + Policy_access + "')";
// SqlCommand cmd = new SqlCommand(strCmd, conn);
// int i = cmd.ExecuteNonQuery();
// conn.Close();
//}
public string FrogotPassword(string usrName, string SecurityQue, string SecurityAnswer)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("sp_VerifySecurity", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@UserName", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@SecurityQue", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@SecurityAnswer", SqlDbType.VarChar));
cmd.Parameters[0].Value = usrName;
cmd.Parameters[1].Value = SecurityQue;
cmd.Parameters[2].Value = SecurityAnswer;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return (ds.Tables[0].Rows[0][0].ToString());
}
public string ValidatePrivateKey(int userId)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("sp_ValidatePrivateKey", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@userId", SqlDbType.Int ));
cmd.Parameters[0].Value = userId;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return (ds.Tables[0].Rows[0][0].ToString());
}
public DataTable SearchKeyword(string input)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
string commandstring = "select name from SalesLT.Product where Name like '%" + input + "%'";
SqlCommand cmd = new SqlCommand(commandstring, conn);
cmd.CommandType = CommandType.Text ;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return (ds.Tables[0]);
}
public DataTable FetchUsers(int userId)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
string commandstring = "SELECT [GmailUserName] FROM [IntrusionDetection].[dbo].[DBALogin]" +
" where ID != " + userId ;
SqlCommand cmd = new SqlCommand(commandstring, conn);
cmd.CommandType = CommandType.Text;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return (ds.Tables[0]);
}
public void UpdateStatus(string username)
{
OpenDB();
string strCmd = "update tblUserDetails set active=0 where username = '" + username + "'";
SqlCommand cmd = new SqlCommand(strCmd, conn);
//int i = 0;
int i = cmd.ExecuteNonQuery();
conn.Close();
}
public string GetPrivateKey(string uname,string pwd,string refNum)
{
OpenDB();
sql = "select PrivateKey from dbo.DBALogin where UserName='" + uname + "' and [Password]='" + pwd + "' and DBAReferenceNumber ='" + refNum + "' ";
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0].Rows[0][0].ToString();
}
public int DBAScriptInsert(string script, int createuserID, string KeyGenerated, string changes, string tbl)
{
OpenDB();
string strCmd = "insert into objectChangeScript(script,createuserID,KeyGenerated,Status,ChangesDone,Tablename) values ('" + script + "'," + createuserID + ",'" + KeyGenerated + "','Pending','" + changes + "','" + tbl + "')";
SqlCommand cmd = new SqlCommand(strCmd, conn);
int i = cmd.ExecuteNonQuery();
InsertForEachDBA(script, createuserID, KeyGenerated);
conn.Close();
return i;
}
public int IndividualDBAUpdate(string script, int userID, string PubliKey, string PrivateKey)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("IndividualDBAUpdate", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@script", SqlDbType.NVarChar));
cmd.Parameters.Add(new SqlParameter("@createuserID", SqlDbType.Int));
cmd.Parameters.Add(new SqlParameter("@PubliKey", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@PrivateKey", SqlDbType.VarChar));
cmd.Parameters[0].Value = script;
cmd.Parameters[1].Value = userID;
cmd.Parameters[2].Value = PubliKey;
cmd.Parameters[3].Value = PrivateKey;
int i = cmd.ExecuteNonQuery();
conn.Close();
return i;
}
public void InsertForEachDBA(string script, int createuserID, string KeyGenerated)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("InsertForEachDBA", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@script", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@createuserID", SqlDbType.Int));
cmd.Parameters.Add(new SqlParameter("@KeyGenerated", SqlDbType.VarChar));
cmd.Parameters[0].Value = script;
cmd.Parameters[1].Value = createuserID;
cmd.Parameters[2].Value = KeyGenerated;
int i = cmd.ExecuteNonQuery();
conn.Close();
}
public DataTable GetDBAApproval(int userid)
{
OpenDB();
sql = "SELECT script FROM dbo.DBAIndividualApproval where status='Pending' and DBAID= " + userid;
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0];
}
public int IndividualDBARejectUpdate(string script, int userID, string PubliKey, string PrivateKey)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand("IndividualDBARejectUpdate", conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter("@script", SqlDbType.NVarChar));
cmd.Parameters.Add(new SqlParameter("@createuserID", SqlDbType.Int));
cmd.Parameters.Add(new SqlParameter("@PubliKey", SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter("@PrivateKey", SqlDbType.VarChar));
cmd.Parameters[0].Value = script;
cmd.Parameters[1].Value = userID;
cmd.Parameters[2].Value = PubliKey;
cmd.Parameters[3].Value = PrivateKey;
int i = cmd.ExecuteNonQuery();
conn.Close();
return i;
}
}
}
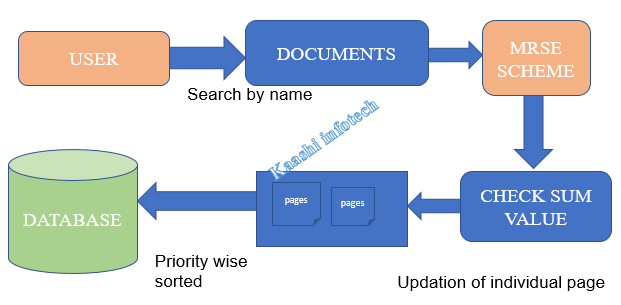
MODULES DESCRIPITION:
-
• New User Registration Module
• Genuine Image Hot Point Check Module
• Fake Image Hot Point Check Module
• Captcha Formation Module
• Authentication Scheme Module
• Admin Unlock Scheme Module
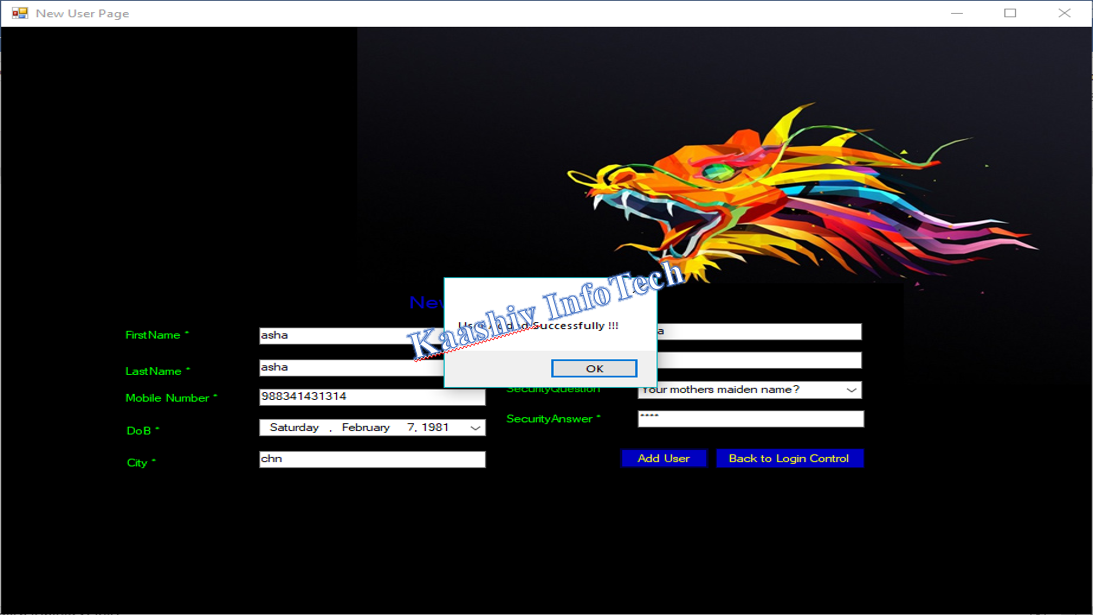
NEW USER REGISTRATION MODULE:
• In this module, the user is permitted to provide the basic authentication information like Username, Password, contact information.
• After providing the user information, the user is permitted to select the images and provide appropriate ranking to those images.
• Once the images were provided with ranking, appropriate image points were selected in the next module.
• In this module, we are providing an option of providing custom images for the user.
• Our system provides a strongest checks on the duplication of ranking and multi selection of images with out a boundary limit.
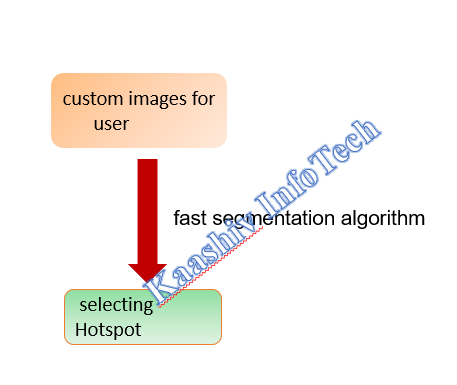
GENUINE IMAGE HOT POINT CHECK MODULE:
• In this module, the users were provided an option of selecting the hotspots in the hierarchy of the images.
• Once the hotspot is identified, the relevant point boundary of the hotspot is identified with the help of fast segmentation algorithm.
• Appropriate pixel values of box shaped were taken to avoid discrepancy in identifying the hotspot during authentication page.
• Once the first level of images were identified for the hotspot, the second level of images were placed for the hotspot. A similar algorithm is implemented to scale up the exact location of the hotspot.
• After that, based on the image ranking for the user, the hotspot on the next level of hierarchical images were identified. This process becomes a recursive process for the successive images.
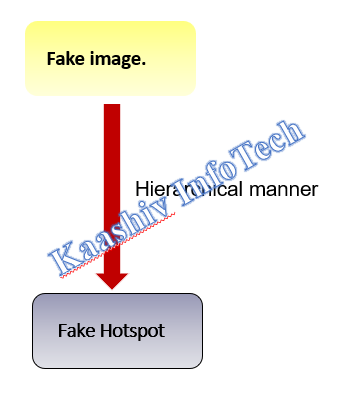
FAKE IMAGE HOT POINT CHECK MODULE:
• In this module, to make the fake users to deviate from the original image. Fake hotspots on the fake images were placed in a hierarchical manner.
• The hotspots will be placed with the help of segmentation algorithm. Appropriate pixel values of box shaped were taken to avoid discrepancy in identifying the hotspot during authentication page.
• The fake images with fake hotspot on the images will increase the complexity of the authentication scheme.
• The process will be followed as specified in the previous modules.
CAPTCHA FORMATION MODULE:
• A most complicated algorithm concept which provides one of the world’s strongest algorithm in the place of authenticating the user.
• Registering the user involves , Minimum length of the password should be 8 and it can be called as secret passcode.
• The secret pass code should contain even number of characters. In our case, we made this one mandatory as 8. Session password will be generated based on this secret pass code
• During the login phase of the project, the user will enter his username an interface consisting of a complex grid which is displayed.
• The Alphanumeric grid consists of numbers and alphabets . These were randomly placed on the data grid and the interface will change every time during user login
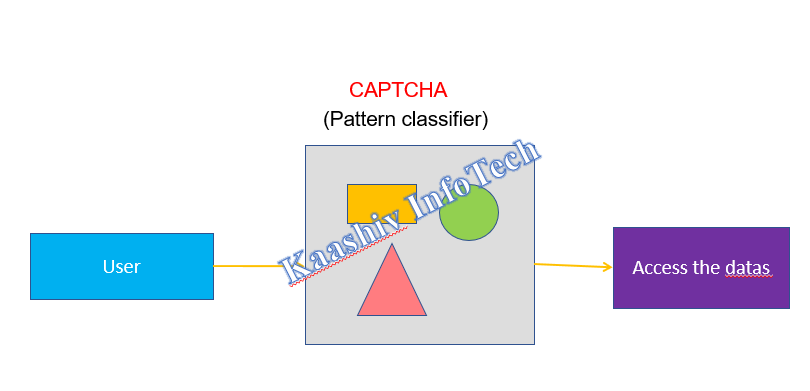
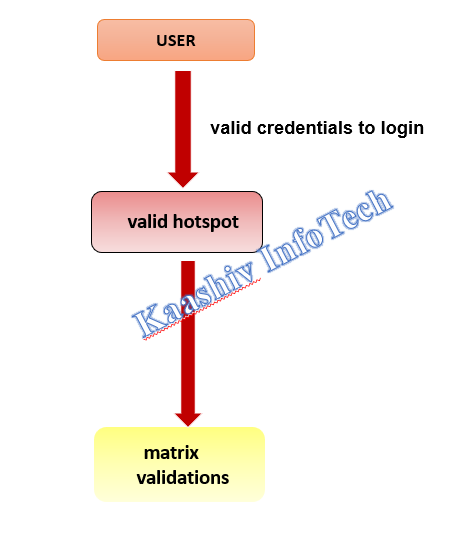
AUTHENTICATION SCHEME MODULE:
• The user will be permitted to provide their valid credentials to login into the system. Before finalizing the validation of the user, they need to cross two level of boundaries.
• The users will be checked for the valid hotspot of the images. Once the user crossed the exact boundaries of valid checks.
• The second check with be the captcha validations. Once the user provides valid Captcha data. He will be permitted to view his profile page.
• If more than a stipulated time, the user have tried the login. In that case, the user will be blocked permanently and it can be overcome by the Admin.
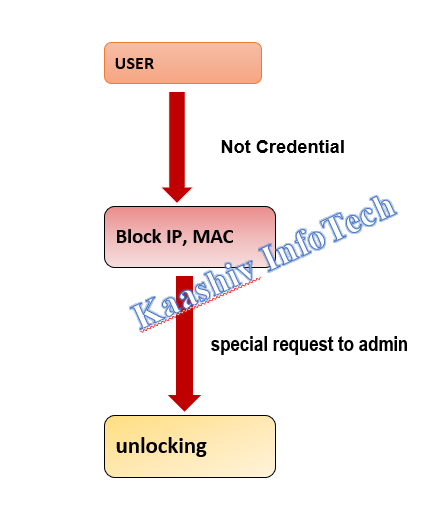
ADMIN UNLOCK SCHEME MODULE
• The users were provided with permissible number of access on the authentication page. • If they couldn’t access the content, in that case the user’s IP Address and MAC address will be blocked by the system to prevent future access on the system. • Once the user needs to access the data, a special request to the admin followed by the admin unlocking the system.
ISO CERTIFIED - FINAL YEAR PROJECTS FOR COMPUTER SCIENCE:
KaaShiv Offers, Final year project for computer science. Final year project for computer science includes Artificial Intelligence, R-programming, web application, Machine Learning, Data Science, cloud computing, EthicalHacking, networking . This internship includes the topics related to final year projects for computer science 2nd year students , final year projects for computer science 3rd year students , final year projects for computer science year students , final year projects for computer science 4th year students.This company runs by,
• 10 Years Awarded Microsoft Most Valuable Professional
• Google Recognized Experts
• Cisco Recognized Certified Experts
• Microsoft Awarded Certified Experts
• Robotics Experts
• HCL Technologies Awarded Expert
Trainers at KaaShiv InfoTech are real-time Software / IT professionals worked in leading MNCs like,
• CTS
• Wipro,
• TCS,
• Infosys,
• Accenture and
• Mindtree.
The Course curriculum for Final year project for computer science is carefully researched and prepared by professionals from MNC to meet the demands expected in the IT industry. After completing the Final year project Training in Chennai at KaaShiv Infotech, students will be familiar with the Software development process followed in IT industry. Below are some of the insights of our Final year project program for computer science ,
• Real-time project development and Technology Training by Microsoft Awarded Most Valuable Professiona
• Final year project for computer science students involves Full practical training
• Hardware and software tools full support
• Technology training
• Placement training
• Full documentation and report analysis
• R & D projects
• Industrial exposure
• Endorsing Corporate skills
WHAT IS FINAL YEAR PROJECT ?
• The Final year projects plays a crucial role in the teaching-learning process.
• It is also a way of identifying the ability of the student to perform an industrial project or applied research linked to the knowledge discipline.
• A project is defined as an effort to create or modify a specific product or service.
• Projects are temporary work efforts with a clear beginning and end.
• Final year project (or program) any undertaking, carried out individually or collaboratively and possibly involving research or design, that is carefully planned (usually by a project team) to achieve a particular aim
WHAT ARE THE BENEFITS GAINED BY DOING FINAL YEAR PROJECT
• final year projects if done well can add a lot of credibility to your profile.
• And especially your final year projects building experience can help you perform well in core job placements & higher studies admission interviews.
TIPS TO SELECT GOOD FINAL YEAR PROJECTS
>
• Analyze the current trends
• Focus your final year project on any social issue
• Get expert’s assistance whenever possible
• Research about the final year projects done by your seniors
• Refer the research journals published by scholars
• Check the feasibility of your final year project
• Work with organizations like Kaashiv InfoTech
WHY, COMPUTER SCIENCE STUDENTS FINAL YEAR PROJECTS SHOULD BE A REAL TIME FINAL YEAR PROJECTS ?
Final year project for computer science students provides a real time exposure for the Final year project for computer science students on the latest and trending technologies. Below are some of the Top jobs in the IT Industry Job Openings ,
• Software Developers – Good in Python, Machine Learning, Data Science and AI programming
• BlockChain Administrators
• IOT Specialists
• Cyber Security
• Web Application Developer – Web Designers
• Information Security Analyst – Security Specialist
• Network Engineers / Analys
KaaShiv Infotech, Final year project for computer science Student - programme hornes you in the above said skills / job roles from basics to Advanced.
FINAL YEAR PROJECT FOR COMPUTER SCIENCE - PROGRAMME HIGHLIGHTS
• Final year project for computer science program duration: 5days/ 10days / Or Any number of days
• Training hours: 3hrs per day
• Software & others tools installation Guidance
• Hardware support
• Final year project for computer science Report creation / Project Report creation
• Final year project for computer science students based 2 projects ( real time)
• Final year project Certificate & Inplant Training Certificate & Industrial exposure certificate + (Achievement certificate for best performers)
ADVANTAGES OF OUR- FINAL YEAR PROJECT FOR COMPUTER SCIENCE
• Get Real Work Experience
• Get a Taste of Your Chosen Field
• Start Networking
• Helps You Choose a Speciality
• Helps You Become More Self-Confident
• Boosts Your CV
• Increases Your Market Value
FINAL YEAR PROJECT FOR COMPUTER SCIENCE - MATERIALS
• Final year project for computer science student , includes Materials after the internship programme
• Technological guidance and materials will be shared in entire year for the students to mold technically.
• Our be student involves Free Projects at the end of the programme.
QUERIES OR CONTACT DETAILS :
Venkat (7667662428) and Asha (7667668009)
EmailID:kaashiv.info@gmail.com ,
priyanka.kaashiv@gmail.com
FINAL YEAR PROJECT FOR COMPUTER SCIENCE- PROGRAMME DURATION :
1 months / 2 months / 3 months to 6 Months ( Any Number of Days - Based on student preferences)
WHO CAN ATTEND THIS FINAL YEAR PROJECT FOR COMPUTER SCIENCE PROGRAMME :
final year project for computer science - Programme can be attended by the students who are looking for final year project for computer science/ final year project for computer science 2nd year/final year project for computer science 3rd year/final year project for computer science 4th year
FINAL YEAR PROJECT FOR COMPUTER SCIENCE - PROGRAMME OUTCOME :
1. Student will be specialized in Block Chain, Artificial Intelligence, Machine Learning, Python and R programming, Application Development
, Web designing and Networking concepts (Basics to Advanced)
2. Covering 45 concepts
3. Students will be getting trained in / writing 45 Programs – Will change based on the durations of the program.
4. 2 Projects and project documents will be given at the end of the program
REFERENCE YOUTUBE URL FOR FINAL YEAR PROJECT FOR COMPUTER SCIENCE :
Check our Internship Training sample videos at this URL –
Check our Internship Training sample videos
REGISTRATION LINK FOR – FINAL YEAR PROJECT FOR COMPUTER SCIENCE :
final year project for computer science - Offline - Office training
Fill our online Internship form
FINAL YEAR PROJECT FOR COMPUTER SCIENCE – DEMO LINK :
Check out our Sample final year project for computer science Content for the training
inplant-training-in-chennai-for-cse-demo
CHECK OUR PREVIOUS TESTIMONIALS FROM STUDENTS FROM DIFFERENT COUNTRIES AND DIFFERENT STATES :
www.kaashivinfotech.com/testimonials/
CHECK OUR STUDENTS FEEDBACK ON OUR - FINAL YEAR PROJECT FOR COMPUTER SCIENCE :
final year project for computer science - Feedback - inplant-training-feedback /
final year project for computer science - Feedback - internship-feedback
CHECK OUT THE COLLEGES ATTENDED OUR FINAL YEAR PROJECT FOR COMPUTER SCIENCE
internship-and-inplant-training-attendees/
CHECK OUR SOCIAL SERVICE YOUTUBE CHANNELS :
Check our Social Service youtube channels
Check our Social Service youtube channels
REAL TIME PROJECT :
We ranked Top 200 technological companies in Tamil Nadu, Click here to view
MORE ON OUR, FINAL YEAR PROJECT FOR COMPUTER SCIENCE:
In our, internship on final year project for computer science- programme below are following different kind of programmes focused such as,
1. Final year project for computer science (or) paid Final year project for computer science,
- Kaashiv Provides an in-depth knowledge of software Platform and other relevant software technologies.
2. Final year project for computer science work from home – Our company provides facility for the students to learn from home as an Final year project for computer science based on latest technological trends.
3. Final year project for computer science report – Reports are also provided for the final year projects for students in our company related.
4. Final year project for computer science jobs – 100% Job assistance will be provided for the students to gain practical knowledge during the Final year project for computer science period in our company.
5. Final yearproject for computer science summer / Winter internship 2019/2020 – Summer / Winter holiday internship in Final year projects will be given to the student based on the developer knowledge base.
6. Final year project for computer science interview questions – We provide top trending and frequently asked question for the intern students during the internship period based on software development and trending technologies.
7. Final year project for computer science test – Based on the students request, if you are looking for any test to validate your knowledge. we are ready to provide the same.
8. Final year project for computer science certificate – Industry recognized certificates will be provided for the students who perform internship in our company based .
9. Final year project for computer science online– Learn Final year projects for computer science from home, our company perform internship through online too.
10. Final year project for computer science ppt / final year projects for computer science / projects report – We provide Final year projects for computer science based ppts. projects and project reports as materials after the internship in our company.
11. Free final year project for computer science - Our company will provide free Final year projects for computer science the best students of kaashiv infotech.
12. Project For Diploma Final year projects for computer science – We offer project for the diploma Final year project for computer science students in our company.
13. Final year project for computer science 2nd Year / 3rd Year / B-Tech Students – Our company offers you final year project for computer science the above students.